
Best Practices for Web Application Security
It is said that “a chain is only as strong as its weakest link”. In terms of Web application security we might consider the end user as the main point of vulnerability.
However, there are methods that can be implemented to reduce the chance of running into web application security problems.
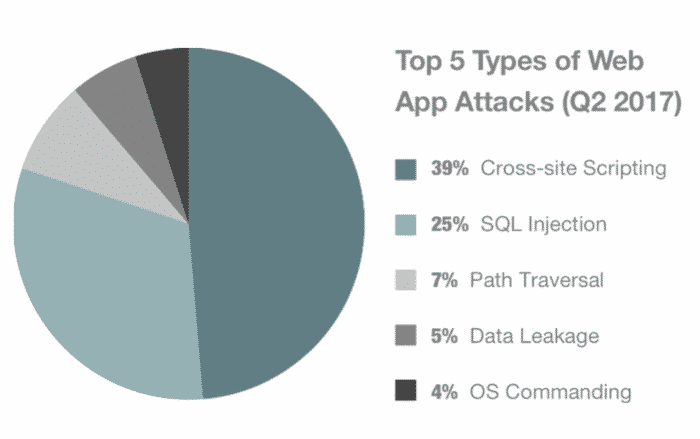
According to cluth these are the top five types of web app attacks.
In this post, we’ve rounded up five particularly important web application security best practices to keep in mind as you harden your web security.
XSS (Cross Site Scripting)
XSS vulnerabilities arise where web applications dynamically include data from users without proper validation. Using JavaScript embedded on a web page, a malicious user can control the victim’s browser bypassing normal security restrictions. To protect against XSS, all scripting tags should be encoded and validated on server-side. Frameworks like JSF provide components for an easy XSS protection.
SQL Injection
SQL injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you an SQL statement that you will unknowingly run on your database. To mitigate vulnerability to SQL injection, every input provided by user should be escaped by special characters. Limiting the permissions on the database to only what is needed may help reduce the effectiveness of potential SQL injection attack.
Vulnerable Data
Any critical data stored in the database must always be encrypted. The same goes for communication between backend and frontend in your application. It is worth to note that confidential data should not be passed via GET requests.
Security Misconfigurations
Security misconfigurations are still common even in the enterprise environment. They occur when a system or database administrator does not properly configure framework of an application or server. Running security scans on a consistent schedule can help stop potential leaks. Also remember to run applications with least privileges and keep files for your Web application in a folder below the application root. Users shouldn’t be able to specify a path for any file access in your application. This helps to prevent users from getting access to the root of your server.
Using Components With Known Vulnerabilities
Vulnerabilities in third-party libraries and software are extremely common and could be used to compromise the security of systems using the software. Since it is virtually impossible to write all the code by yourself, keep in mind that regularly upgrading components to new versions is critical. Tools like OWASP Dependency-Check will help you identify project dependencies and check if there are any known, publicly disclosed, vulnerabilities.
Wow, that’s what I was exploring for, what a information! present here at
this blog, thanks admin of this web page.
The pleasure is ours 🙂 We are pleased that you liked our content!